WHY IAST?
See and secure everything you code and run.
VISIBILITY
Say bye-bye to blind spots.
- See all protected and unprotected applications to quickly spot hidden threats early.
- Understand associated relationships with context-driven insights.
- Continuously monitor and confirm remediation status to close security gaps.
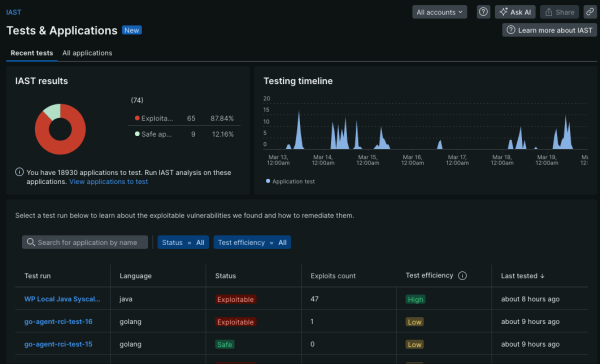
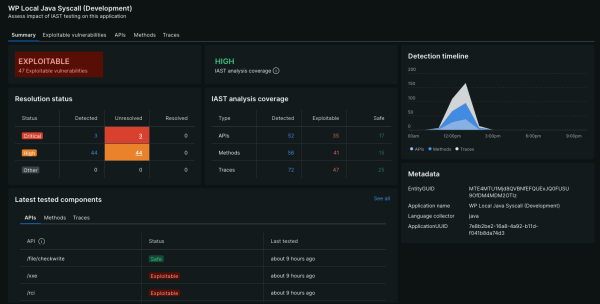
UNMATCHED ACCURACY
Accurately pinpoint where vulnerabilities exist.
- Easily identify vulnerabilities in real time across all layers of the application stack.
- Eliminate false positives with fast, accurate detection of real security risks with automated validation.
- Give developers vulnerability lists prioritized by risk to easily focus on what matters most.
PROACTIVE SECURITY
Find, fix, and verify high-risk vulnerabilities.
- Test and confirm vulnerabilities with proof of exploit before they become problems.
- Test code quickly and easily in development, without waiting for separate security testing.
- See all observability and security data together and use it to enhance context for the most effective remediation.
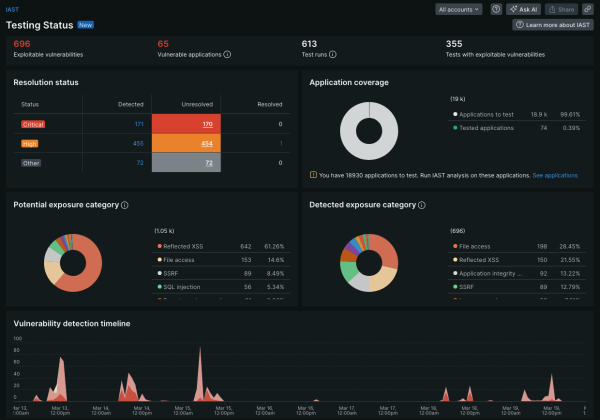
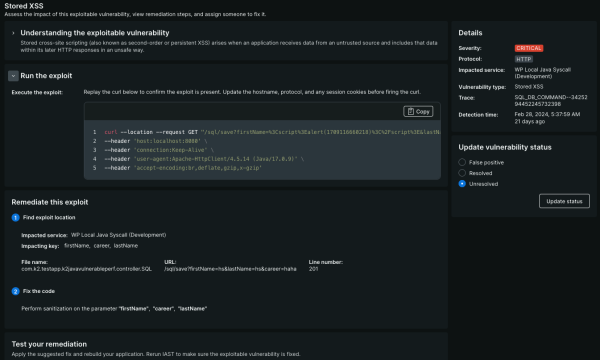
ACCELERATED REMEDIATION
Fix vulnerabilities faster than ever.
- Avoid critical mistakes with guided remediation and guardrails to easily keep development on track.
- Eliminate security risks by tracking and monitoring the status of every remediation effort.
- Make it easier for developers to build more secure code with a continuous feedback loop.
Look who
has us open.
has us open.
1